Burp Suite Intruder
Created On 18. Jun 2020
Updated: 2021-05-01 23:58:45.259899000 +0000
Created By: acidghost
As mentioned briefly in the vulnerability mapping section, burp suite is a powerful tool that allows to implement various kinds of attacks.
Burp Proxy
To play with Burp, you will need to get its certificate, because not all browsers will allow out of the box its own one. To use it with Firefox you will have to configure your proxy in browser to 127.0.0.1 on port 8080. After that, start Burp and in your browser navigate to http://burpsuite and download the certificate and then add it to trusted ones in Firefox.
The examples here cover just a little on how to work with Burp. To keep getting better, you will want to read and brainstorm on your solutions at first here https://portswigger.net
Go Proxy -> Intercept -> intercept on/off to interact with the request or not.
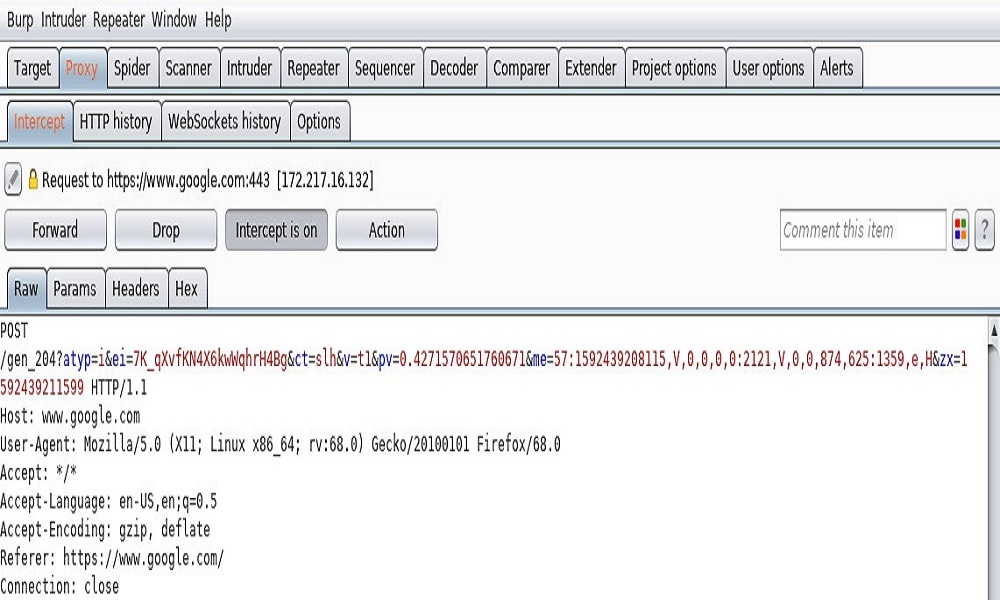
Play with Metasploitable and Burp
Navigate to the Metasploitable IP and go to Mutillidae app in browser and intercept.
Go Target -> Site map: there you will see Mutillidae and click right to add to scope. Scope defines where automated spidering and testing could occur and helps to not actively scan domains that we don't need.
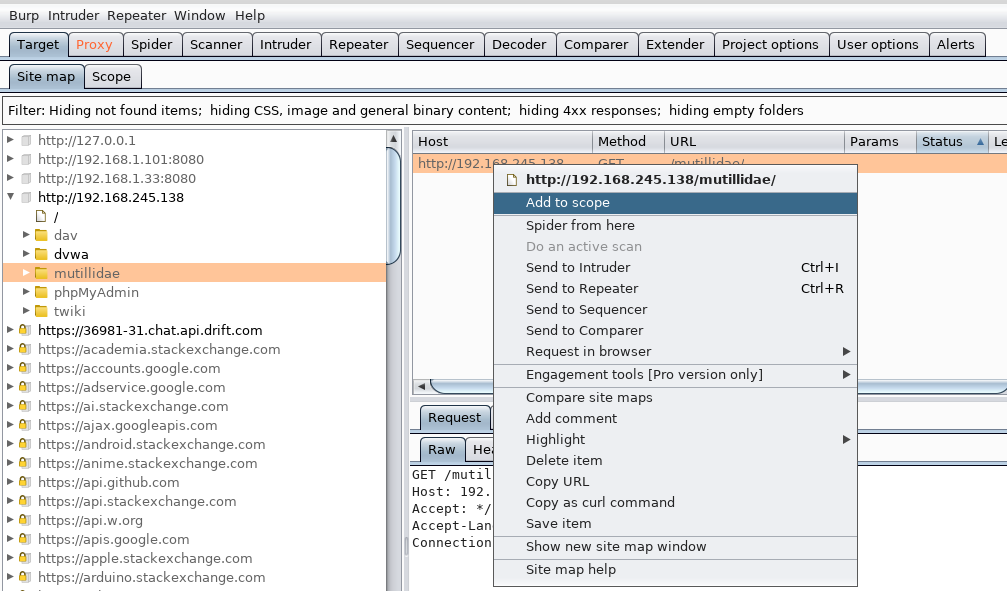
Spider the host and crawl the site to record all https methods. This helps get the structure of the web app, altogether with all references and overall its layout.
For this we can click on our Mutillidae path and right click -> spider this branch.
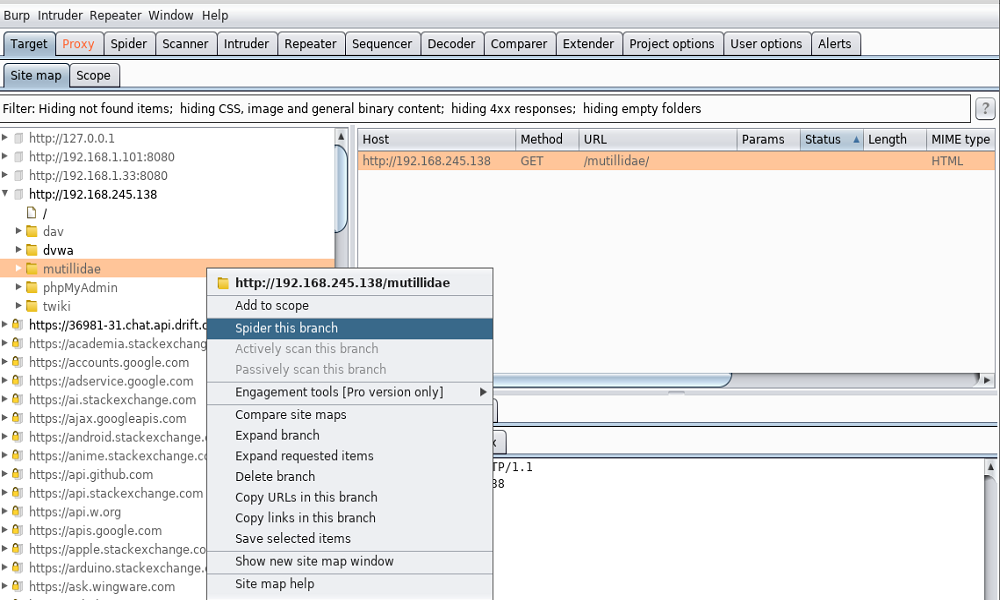
We can check the request and response below the list. In the folder of the app we can see the structure of the site. Below Site Map tab there is a filter option. You can play a bit to adjust better to available options.
Brute force access to app
If you want to sharpen you skills a bit more, you can follow the steps bellow yourself and see how it works out on your side.
Navigate to brute force in DVWA. Then try to login. Then go Proxy -> Action -> Send to Intruder. Then go to Intruder tab and under positions and select our password in text and click 'add' to add a payload. Then go to payloads and select a file for our brute force. When all done select Intruder on the top (not the tab used before) and start the attack. Check the results and verify for a differences. Get two different responses and send to Comparer. Responses are differentiated by their length, status codes etc. Then go to Comparer tab and compare by words. There you will see highlighted the differences in response. This will give you hints how the app responded to different passwords during brute forcing.
Burp Discover Content [PRO]
This feature allows to discover pages that are hidden publicly, as for example login. It helps bypassing auth process.
Go Mutillidae and spider it. In Spider -> Options look for Application Login and change in field to use a smart SQL injection.
Then go to Mutillidae folder and click spider this branch. We can see in tab Spider -> Control the status.
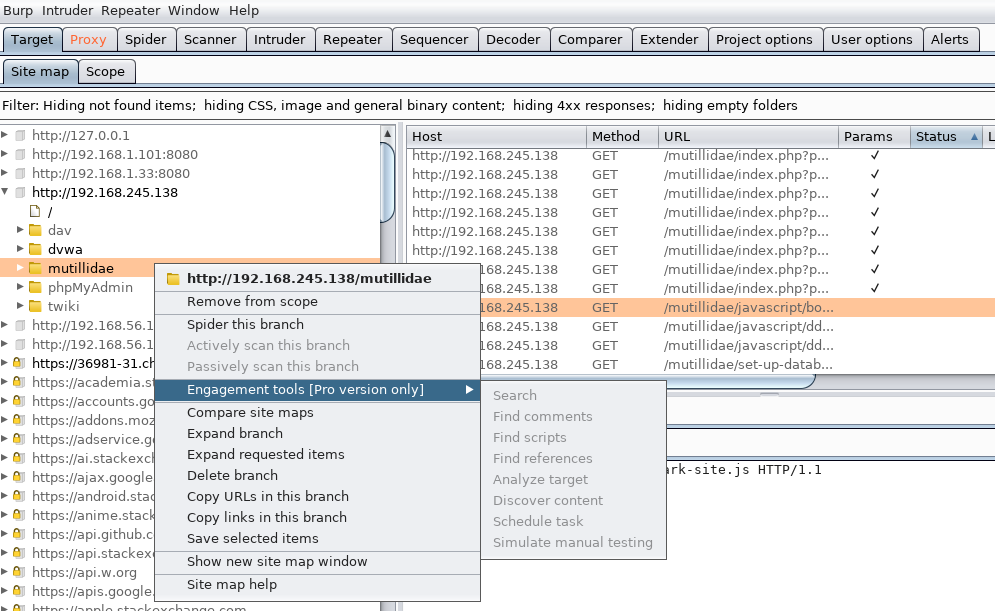
Then we go our app folder and click Engagement Tool -> Discover content.
If you have the Pro version, you should see the brute force results in Site Map.
Using own code with Burp
Burp allows to use own tools in the Extender tab. In itself it is all java, but luckily with Extender you can use ruby, java or python code to automate your code on top of Burp.
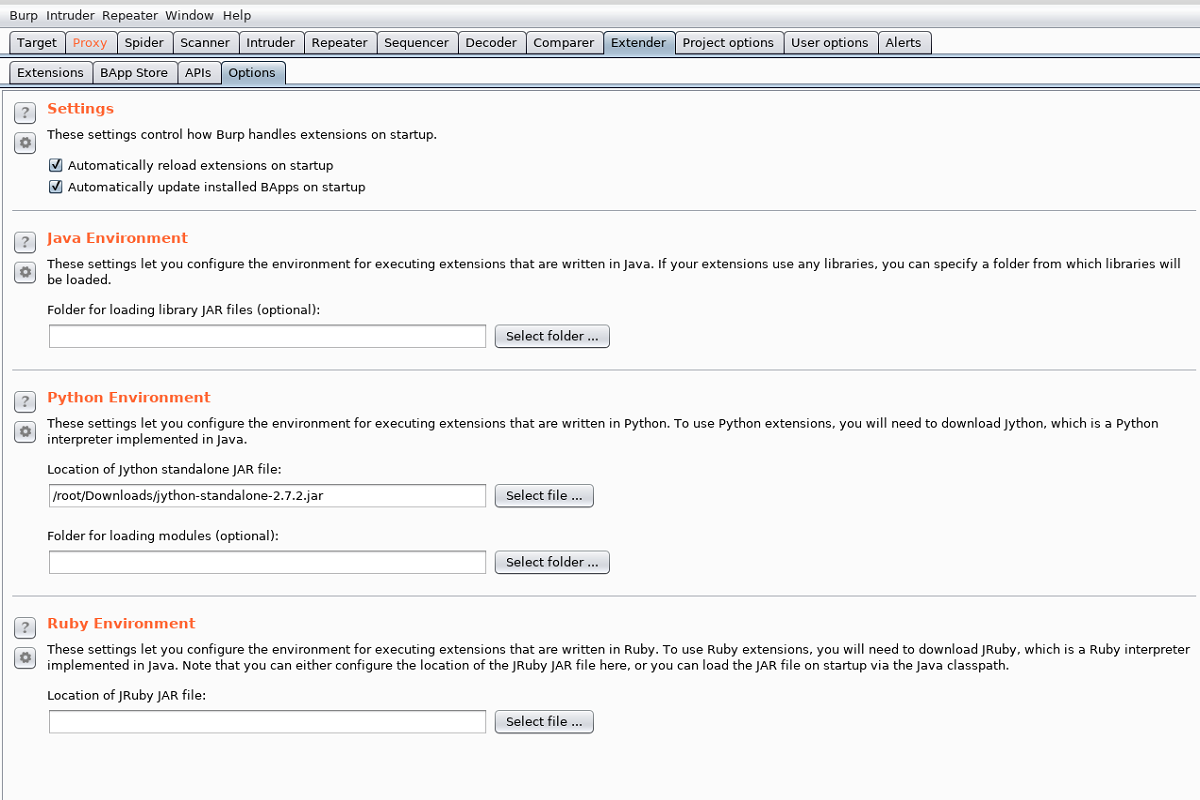
To work with python, download the jython jar file from here https://www.jython.org/download and add it in Burp under Extender -> Options tab.
Then punch in this code and save it as a .py file.
from burp import IBurpExtender
from burp import IIntruderPayloadGeneratorFactory
from burp import IIntruderPayloadGenerator
from java.util import List, ArrayList
import random
class BurpExtender(IBurpExtender, IIntruderPayloadGeneratorFactory):
def registerExtenderCallbacks(self, callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.registerIntruderPayloadGeneratorFactory(self)
return
def getGeneratorName(self):
return "BHP Payload GeneratoRRRRRR"
def createNewInstance(self, attack):
return BHPFuzzer(self, attack)
class BHPFuzzer(IIntruderPayloadGenerator):
def __init__(self, extender, attack):
self._extender = extender
self._helpers = extender._helpers
self._attack = attack
print "BHP Fuzzer initialized"
self.max_payloads = 10
self.num_payloads = 0
return
def hasMorePayloads(self):
print "hasMorePayloads called."
if self.num_payloads == self.max_payloads:
print "No more payloads."
return True
def getNextPayload(self,current_payload):
# convert into a string
payload = "".join(chr(x) for x in current_payload)
# call our simple mutator to fuzz the POST
payload = self.mutate_payload(payload)
# increase the number of fuzzing attempts
self.num_payloads += 1
return payload
def reset(self):
self.num_payloads = 0
return
def mutate_payload(self,original_payload):
# select a random offset in the payload to mutate
offset = random.randint(0,len(original_payload)-1)
payload = original_payload[:offset]
# random offset insert a SQL injection attempt
payload += "'"
# add the remaining bits of the payload
payload += original_payload[offset:]
return payload
Also accessible here
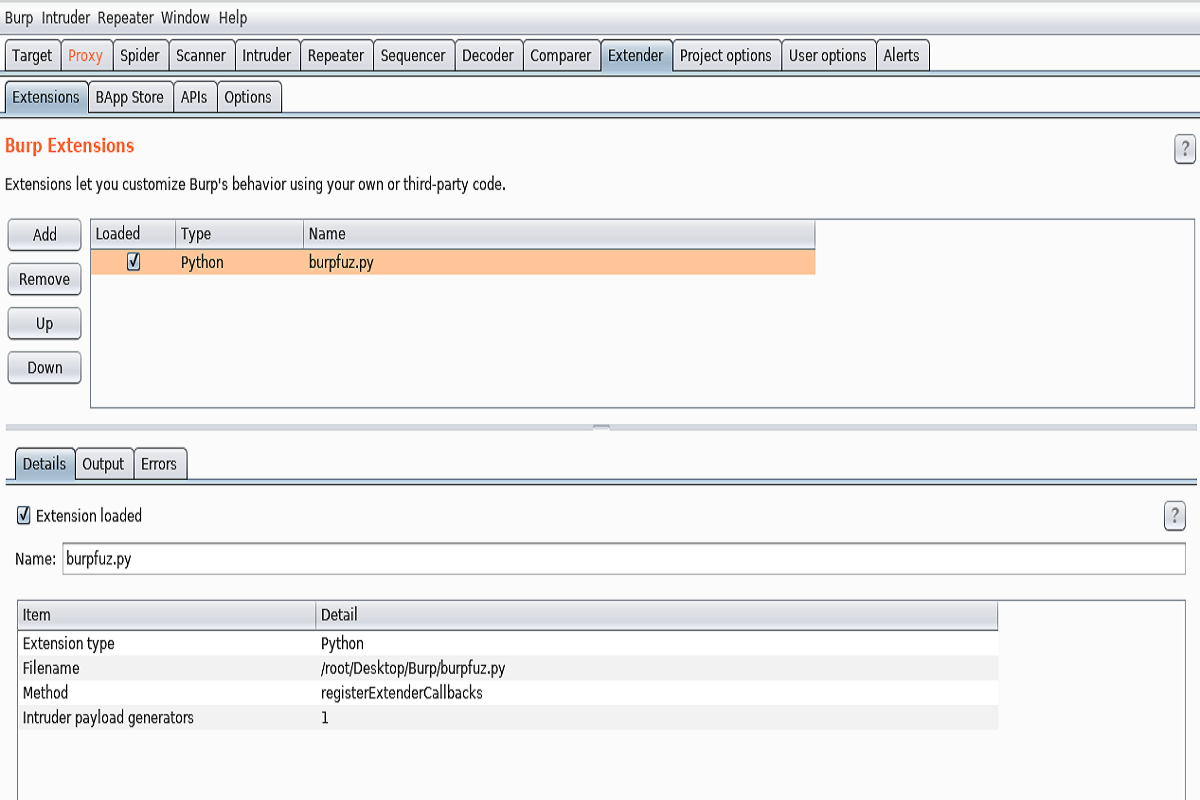
Add it to Extender -> Extensions and check that it loads fine.
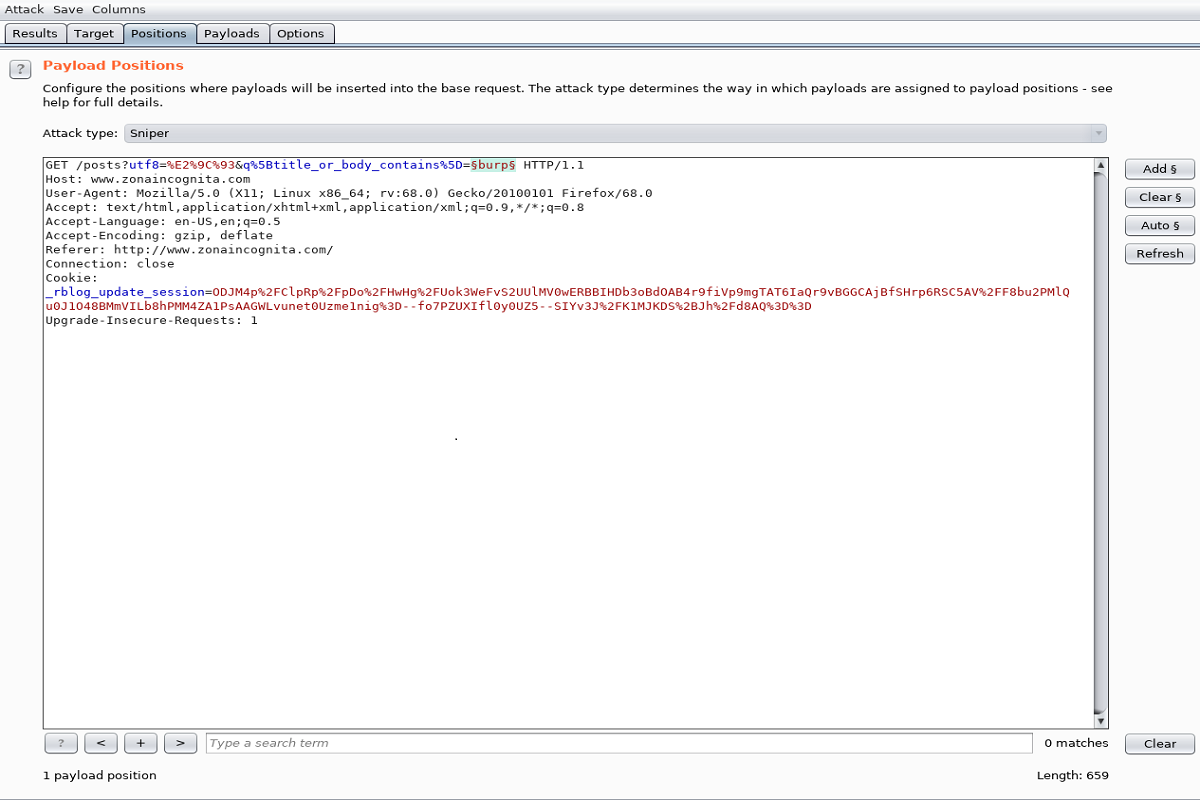
Afterwards navigate to search bar on this web page and type 'burp' with Intercept On.
In Proxy -> HTTP History tab find the request and on right click send it to intruder.
In the Intruder tab navigate to Positions and add just our 'burp' keyword.
From there go to Payloads tab and change the Payload type to Extension Generated and select the generator.
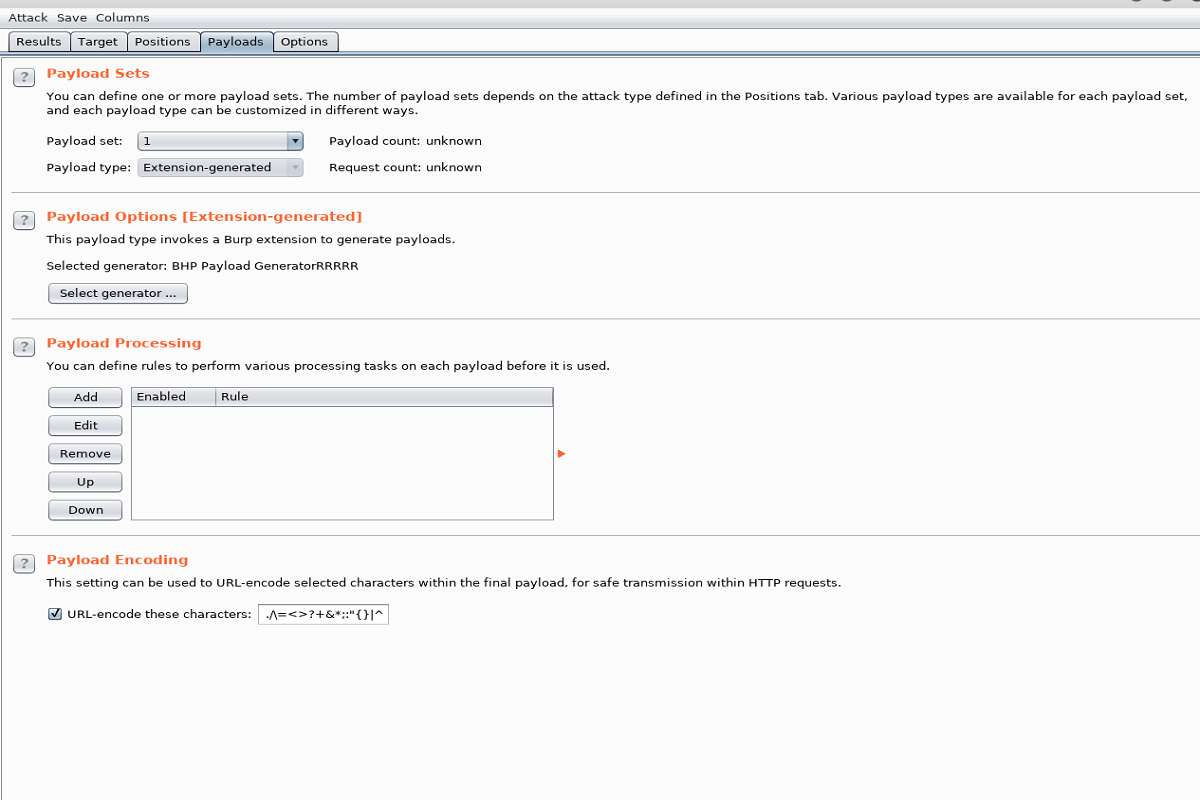
Now push Start Attack and you can see our payload in action in the Results tab.
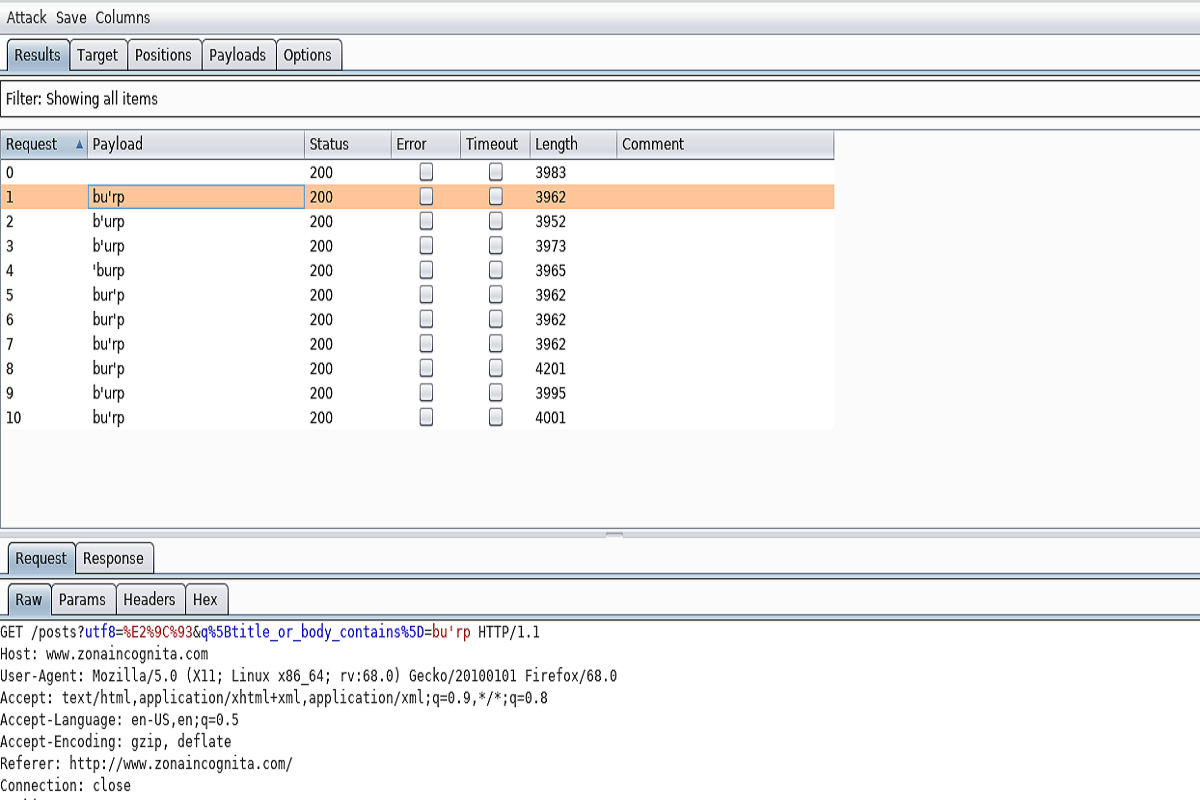
Unfortunately, this seems not enough to trigger an SQL Injection here, but you see how this way it is easy to mess with different payloads. You can extend the code and add more payloads in mutate_payload method.
The code example was inspired from Black Hat Python by Justin Seitz, and if you liked this part, you should definitively read that book, as there are more cool examples how to do and not just this!
Section: Web
Back